Are you ready to crack a mystery and get your hands on that elusive PicoCTF flag? Well, buckle up because we’re diving into the world of PicoCTF Includes Walkthrough. Don’t worry, I’ll keep it fun, and we’ll get to the flag without breaking a sweat. 🏴
Step 1: The First Glance – All You See Is a Simple Page
So, you land on a page that looks like… well, just another page. We’ve all been there, thinking, “What’s this, a plain HTML document?” You might see a button, a little JavaScript magic, and a header saying “On Includes.” Don’t let the simplicity fool you, though! There’s always more under the hood.
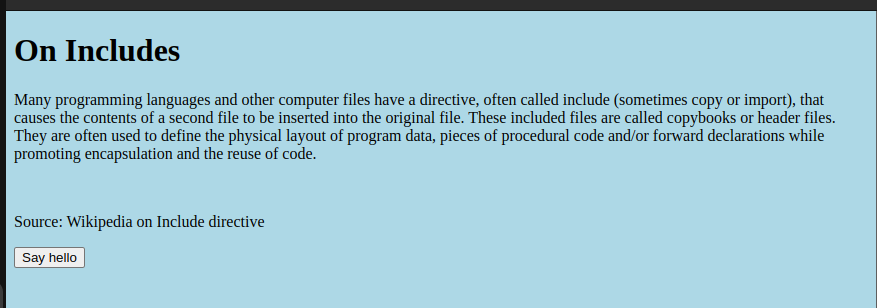
But Wait! There’s More!
As per the hint, this challenge isn’t just about what you see. It’s about what you don’t see. Sometimes, there’s more code hiding in the shadows, and this is where things get juicy.
Step 2: Inspect the Code – The Hidden Secrets in Plain Sight
What do you do when you get stuck in an online challenge? You open the developer tools and start inspecting the page. Here’s the twist: when you open up the inspector, everything looks pretty basic. But, remember that hint: Is there more code than what the inspector initially shows?
The CSS File – A Sneaky Peek at the Flag
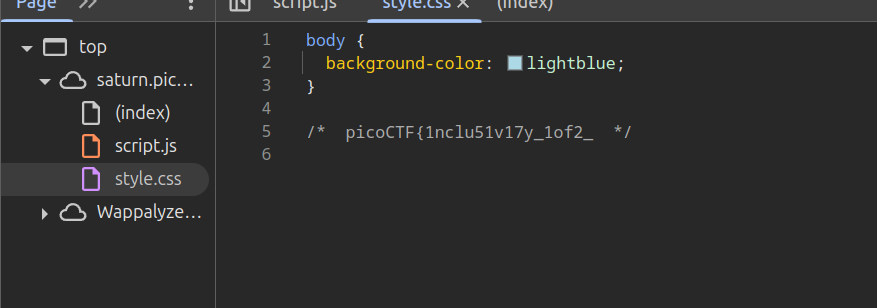
When you open the CSS file, things get a little more interesting. You’ll spot a comment halfway through the code:
picoCTF{1nclu51v17y_1of2_Hold up! That’s part of the flag! Half of it, in fact. Looks like the flag is scattered, and you’ll need the other part to make sense of it. But where’s the rest?
Step 3: Let’s Check the JavaScript – Ah, There It Is!
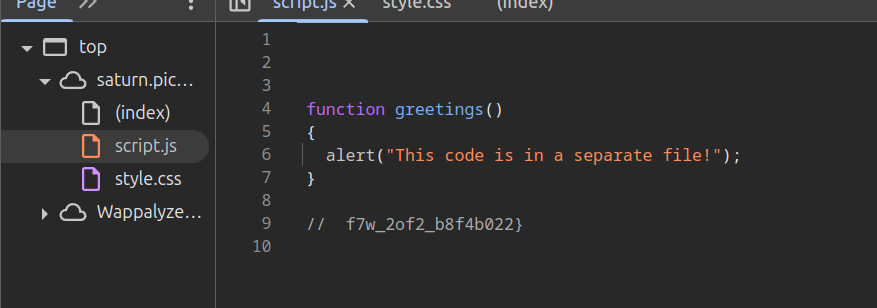
Next, you take a peek at the JavaScript file (you know you’re getting closer now). Inside, you’ll find the second half of the flag, hidden in a little function called greetings(). This little gem will pop up an alert when clicked:
javascriptCopyfunction greetings() {
alert("This code is in a separate file!");
}
// f7w_2of2_b8f4b022}
Now, let’s put the two halves together! Combine the pieces from the CSS and JavaScript files, and bam! You’ve got yourself the full flag:
picoCTF{1nclu51v17y_1of2_f7w_2of2_b8f4b022}Step 4: Get the Flag and Brag About It!
Congrats! You’ve solved the challenge! It wasn’t about cracking complex cryptography or deciphering impossible puzzles. All you had to do was look closer, inspect a few files, and connect the dots. It’s simple, right?
Why Did This Work?
- Hidden in Plain Sight: The flag was split across different files (CSS and JavaScript), so you needed to peek into both to see the full picture.
- Attention to Detail: The key to winning PicoCTF challenges is often hidden in subtle details, like comments in the code or functions that seem innocent but hold secrets.
Pro Tips for Future Challenges
- Inspect Everything: Don’t just look at what’s visible in the browser. Check the source files, hidden scripts, and even comments.
- Stay Curious: Some flags are as easy to find as pie if you just take the time to look in the right place.
And that’s a wrap for your PicoCTF Includes Walkthrough! The flag is yours, and you’ve learned a valuable lesson: Never trust what’s on the surface. Happy hacking!