Honeypot in Cybersecurity – A Sneaky Trap for Sneakier Hackers
Let’s face it—hackers are like raccoons. They’ll dig through your digital trash just to find something juicy. And no matter how high your firewall stands, or how secure your VPN seems, some pesky attacker might still find their way in. That’s where the honeypot comes in. 🕵️
No, it’s not honey. No bears involved. But it’s sweet—if you’re into catching cyber criminals in the act.
So, What the Heck Is a Honeypot?
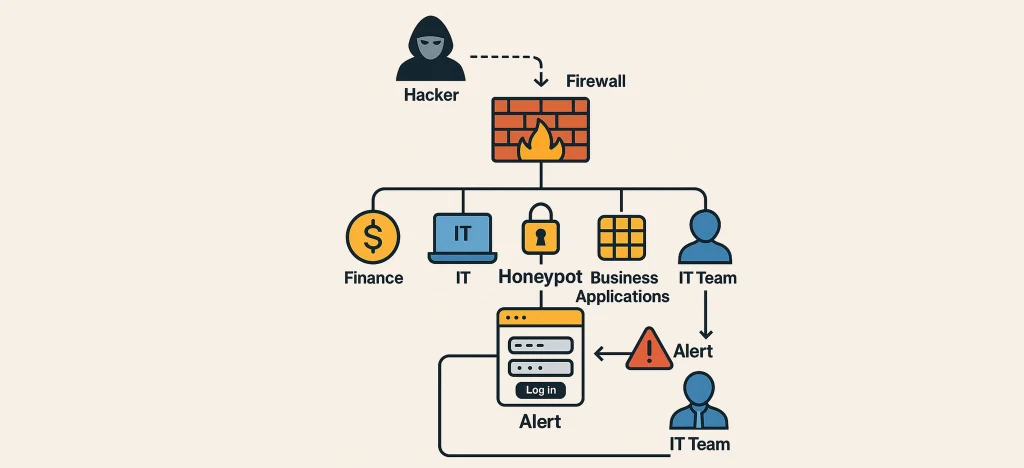
Imagine this: You’re walking through a corporate network, pretending to be an attacker (don’t actually do this). You spot a login page that looks like it belongs to something important—finance, HR, or maybe the “Top Secret Pizza Order Tracker.” You think, “Aha! Jackpot!”
But nope. That’s a honeypot, my friend.
Here’s What It Does:
- It looks real—like a finance or IT login portal.
- It’s fake—but very convincing.
- It’s designed to attract hackers—like a flame to a cyber-moth.
- It alerts the security team when someone tries to access it.
Basically, it’s like leaving out free cookies labeled “Not Poisoned” to catch cookie thieves.
Why Do Organizations Use Honeypots?
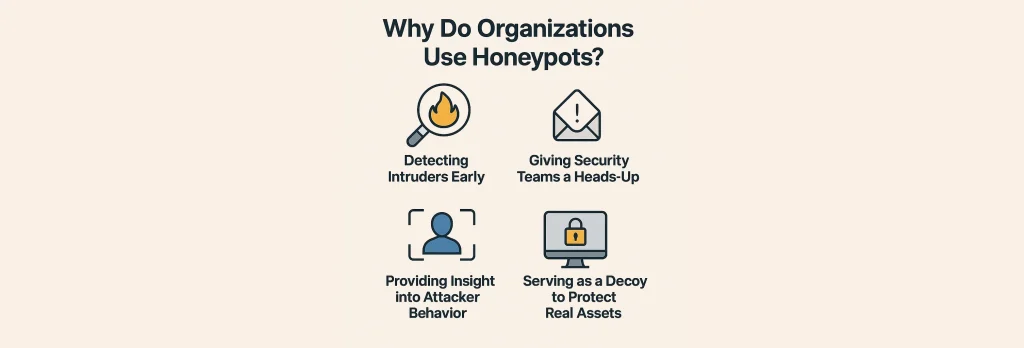
Because firewalls alone aren’t enough. You might have the Fort Knox of routers, but hackers are clever—like your nosy coworker who always “accidentally” opens your browser tabs.
Honeypots help by:
- Detecting intruders early
- Giving security teams a heads-up
- Providing insight into attacker behavior
- Serving as a decoy to protect real assets
It’s not just defense—it’s digital bait with brains.
How Honeypots Actually Work (Without Getting Too Nerdy)
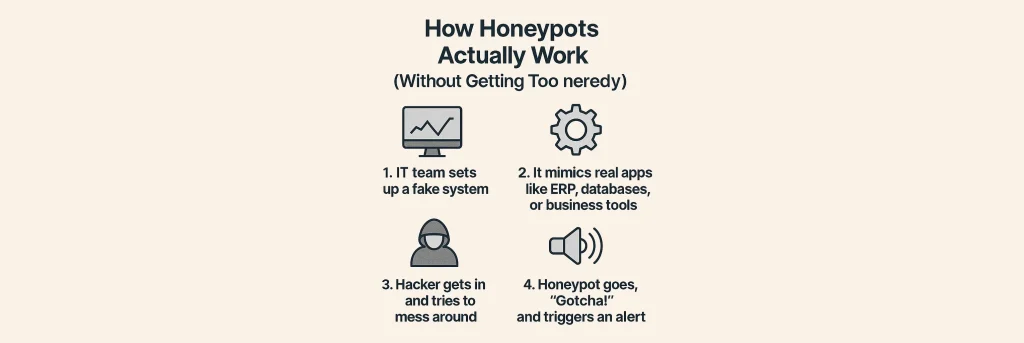
- IT team sets up a fake system.
- It mimics real apps like ERP, databases, or business tools.
- Hacker gets in and tries to mess around.
- Honeypot goes, “Gotcha!” and triggers an alert.
- IT security team jumps into action faster than you on a Friday at 4:59 PM.
It’s basically a booby trap—but in ones and zeros.
Real-Life Use Case (No Sci-Fi Needed)
Say your company subscribes to a service like Blue Maris Security. It includes honeypots as part of its defense system.
One day, some cyber-villain tries logging into your fake finance system. The honeypot detects it, logs everything the attacker does, and alerts your IT team before any real damage is done.
It’s like catching a cat burglar walking into a decoy jewelry store that only sells glitter and regret.
SEO Benefits of Using Honeypots (Because Yes, Even Hackers Boost Your Visibility)
Okay, not directly. But if you run a cybersecurity business or write tech content, including honeypot strategies:
- Shows your cyber-savviness
- Improves trust and authority in your niche
- Can attract links from high-authority sources like OWASP or CISA
Wrapping It Up – Honeypots Are the Cybersecurity Equivalent of a Fake Mustache and a Trap Door
A honeypot in cybersecurity is a clever, proactive defense mechanism. It doesn’t just block intruders—it fools them, watches them, and alerts the pros to take them down.
So if your firewall is the front door, think of the honeypot as the unlocked window… with a security camera, a tripwire, and maybe a bucket of glitter above it. 🎯
Key Takeaways (In Case You Skimmed Like a True 2025 Internet User)
- A honeypot is a fake system used to detect unauthorized access.
- It helps cybersecurity teams detect threats early.
- It’s often part of a broader network defense strategy.
- It’s cooler than your neighbor’s Wi-Fi name (“VirusDetected_21”).