So, you’ve found yourself stuck on the picoCTF Apriti Sesamo Walkthrough challenge? Don’t worry, you’re not alone! The challenge looks tricky at first, but we’re about to break it down with some clever tricks and a little bit of hacker magic. Think of this as the treasure map to finding the flag, with a few hidden clues sprinkled in. Ready to roll up your sleeves? Let’s get hacking!
Introduction to picoCTF Apriti Sesamo Challenge
Alright, so we’ve got this challenge in the picoCTF competition called Apriti Sesamo. Sounds all fancy and mysterious, right? Well, it’s a web-based challenge, and we’re supposed to hack into it, which is where the fun begins.
The challenge gives us a login page and—wait for it—gives us absolutely no way to log in. Why? Because we can’t! But don’t worry, the developers have been kind enough to leave us some hints. You know, like breadcrumbs for the hacker in all of us. And trust me, this is the kind of puzzle where we’ll need a little crafty thinking to get through.
The Hints You Need
Here’s the deal: The hints we get from the developers are:
- Backup files – Interesting. We know backup files usually have weird extensions like
.bak,.backup,.old, or, my personal favorite, tilde~. - Militant Emacs user – Now this is a chef’s kiss kind of hint. Developers who love Emacs often create backup files with the
~symbol. Classic!
Let’s Take a Peek at the PHP Code
We got redirected to a file called impossibleLogin.php. And after some thinking, and adding the infamous ~, boom! The page source opens up, and we see some PHP code. Now, hold on tight because we’re going to deep-dive into that code to figure out the logic behind this whole thing.
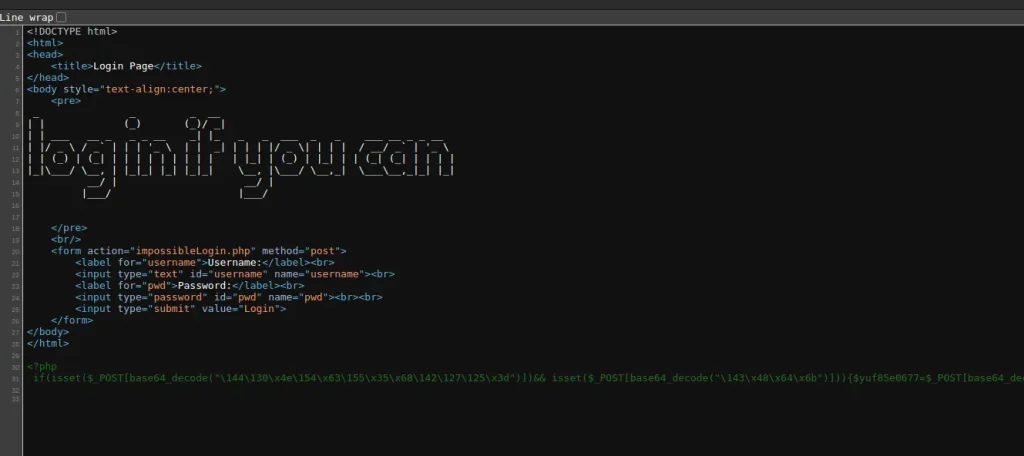
Here’s what we find:
<?php
if(isset($_POST["username"]) && isset($_POST["password"])) {
$yuf85e0677 = $_POST["username"];
$rs35c246d5 = $_POST["password"];
if($yuf85e0677 == $rs35c246d5) {
echo "Success";
} else {
if(sha1($yuf85e0677) === sha1($rs35c246d5)) {
echo file_get_contents("../flag.txt");
} else {
echo "Success";
}
}
}
?>
Let’s Break It Down Like a Detective
This code is like a mini logic puzzle. Here’s what’s going on:
- First, we check if the
usernameandpasswordare set in the POST request. - Then, it checks if the
usernameis equal to thepassword. If they are, it just says “Success”. Easy, right? But we don’t want just success; we want that flag. - If they aren’t the same, it compares the SHA-1 hash of both fields (
sha1($yuf85e0677)andsha1($rs35c246d5)).
If The SHA-1 Hashes Match…
…it reads the flag from the file ../flag.txt and displays it! Whoa! That’s what we’re after!
But Wait! There’s a Twist!
- If the hashes don’t match, the code defaults to saying “Success”, and well, that’s pretty much a dead end for us. We need to make sure those hashes do match, but we don’t want to generate the same hashes manually (because let’s be honest, who has the time for that?).
How Did We Actually Solve picoCTF Apriti Sesamo?
The Trick with Arrays
Here’s where we put on our hacker hats (it’s getting real now).
We intercept the request using a tool like Burp Suite (or any other proxy tool that lets you manipulate HTTP requests). Now, instead of submitting the regular login form like this:
username=123&pwd=456
We submit the parameters as arrays instead:
username[]=123&pwd[]=456

we got flag
What Happens When We Do That? (picoCTF Apriti Sesamo)
You’re probably thinking, “What’s the big deal with arrays?” Well, here’s the magic:
- PHP’s
sha1()function doesn’t like arrays. When we send theusername[]andpwd[]as arrays, PHP throws a warning and returns null for both the username and password hashes. - This means the condition
sha1($yuf85e0677) === sha1($rs35c246d5)becomesnull === null. - Guess what?
null === nullis true! And because of that, PHP goes ahead and shows us the contents of../flag.txt.
Boom, we got the flag!

the flag is:
picoCTF{w3Ll_d3sErV3d_Ch4mp_233d4a80}
Quick Recap: How We Cracked the Code
Step-by-Step Solution
- Identify the Login Issue: The login page gave us no chance to log in. But we spotted a clue—backup files and a militant Emacs user. Nice!
- Look at the PHP Code: We examined the PHP code and saw that it checks the equality of
usernameandpasswordand then compares their SHA-1 hashes. - Send Data as Arrays: Instead of sending strings, we modified the POST request to send
username[]andpwd[]as arrays. - Bypass SHA-1 Check: PHP couldn’t hash arrays, so it returned
nullfor both hashes, which made the conditionnull === nulltrue. - Access the Flag: The code finally displayed the contents of
../flag.txt, revealing the flag!
Final Thoughts on This Challenge (picoCTF Apriti Sesamo)
This was a fun one! The cleverness of this challenge lies in understanding how PHP handles arrays with its sha1() function. Sometimes, the simplest tweaks can lead to big rewards—and in this case, that reward was the flag!