Welcome to our PicoCTF 3v@l walkthrough, where we’re about to explore the exciting world of web exploitation! In this challenge, we’re diving into ABC Bank’s loan calculator, a website that lets users compute loan payments. But here’s the twist: the calculator uses the infamous eval() function, which—if not properly sanitized—can lead to Remote Code Execution (RCE). Our goal? To bypass security measures, exploit the vulnerability, and grab the flag from the server.

If you’re here to learn how to hack a loan calculator (ethically, of course), you’ve come to the right place. Let’s break down this challenge step by step and see how we can bypass restrictions, execute system commands, and retrieve the flag. Ready? Let’s go!
What’s the Problem with eval()?
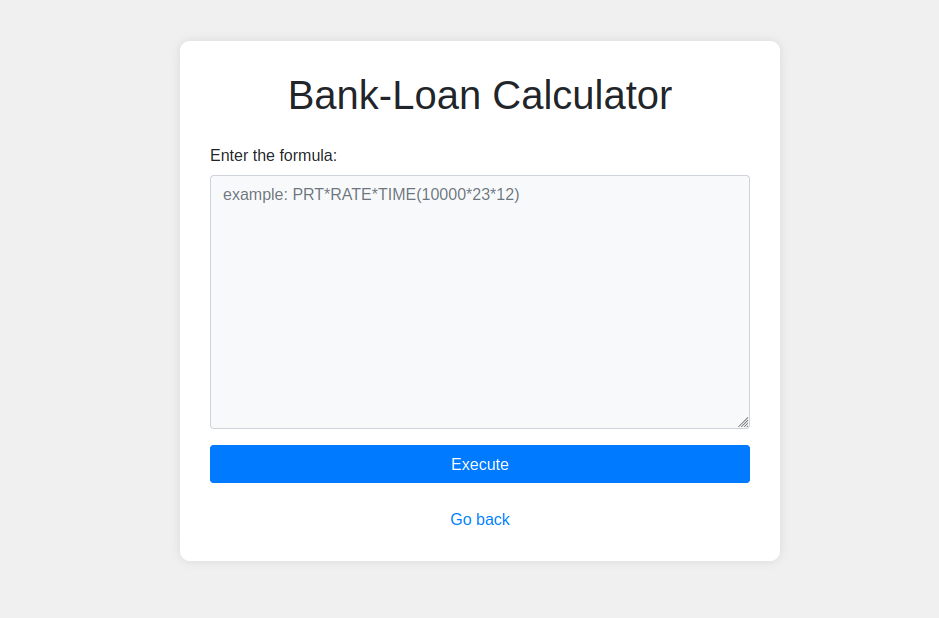
The eval() function, in its simplest form, allows a user’s input to be executed as code. While it can be useful, it’s like giving a stranger a key to your house and asking them to decorate it. If someone’s input isn’t sanitized, they could easily run malicious code. In this case, we can exploit the calculator’s use of eval() to execute commands on the server—giving us the power to fetch the flag.
PicoCTF 3v@l Walkthrough isn’t just about cracking the eval() function; it’s about using our wits to break the website’s security and prove that bad code decisions can have big consequences.
Step 1: Bypass Regex Filters
Before we dive into payload creation, the site tries to filter out malicious input using regex. They think they can stop us with their filters—but little do they know, we’re sneaky! We need to find a way to bypass these filters and make our code invisible to the site’s security measures.
Our strategy? Encoding or dynamically constructing our input so that it doesn’t trip the filters.
Step 2: Dynamically Import subprocess
Now, let’s get to the fun part. We want to execute system commands, but we can’t just call subprocess directly. That would be too obvious. Instead, we’ll use the dynamic import method:
__import__('subprocess')This clever trick lets us bring in the subprocess module without directly invoking it. Now, we’ve got access to system commands without alerting the site’s defenses.
Step 3: Access check_output() via getattr()
Once we’ve got subprocess in play, we need to call the check_output() function to run our system command. But again, we can’t call it directly. So, let’s use getattr() to access it dynamically:
getattr(__import__('subprocess'), 'check_output')Boom! We’ve now got a way to execute system commands on the server—without triggering any alerts.
Step 4: Bypass String Filters Using chr()
At this point, we’re still not out of the woods. The site might be filtering out strings like cat /flag.txt (the command we need to run to get the flag). No worries! We’ll encode this string using ASCII values to sneak it past the filters.
Here’s how we break it down:
chr(99) + chr(97) + chr(116) # "cat"
chr(47) + chr(102) + chr(108) + chr(97) + chr(103) + chr(46) + chr(116) + chr(120) + chr(116) # "/flag.txt"Using chr(), we’re creating the string “cat /flag.txt” from individual characters. This helps us bypass string-based filters that would block the command.
Step 5: Execute the Command
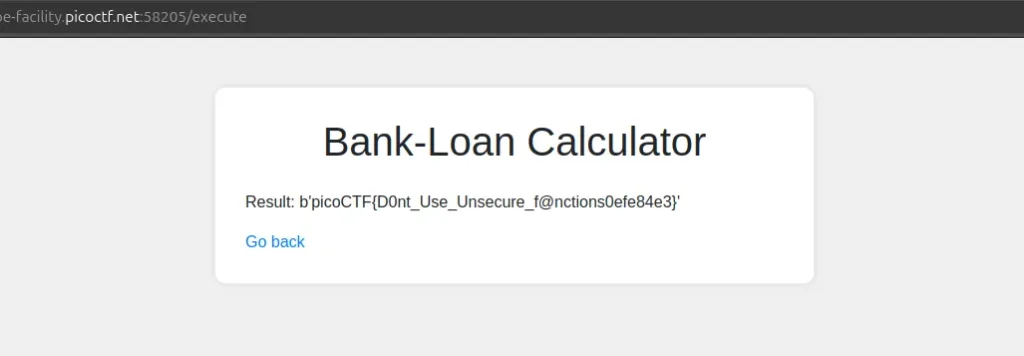
Now for the grand finale: executing the command to get the flag! We use check_output() to run the command and retrieve the contents of /flag.txt.
getattr(__import__('subprocess'), 'check_output')([chr(99)+chr(97)+chr(116), chr(47)+chr(102)+chr(108)+chr(97)+chr(103)+chr(46)+chr(116)+chr(120)+chr(116)])And just like that, we’ve executed the cat /flag.txt command and retrieved the flag.
Why This Works
- Avoids Blacklists: By using dynamic imports and function calls, we avoid triggering any blacklists that would block direct calls like
subprocess.check_output(). - Bypasses String Filters: The use of chr() ensures that strings like cat /flag.txt don’t raise any red flags with the website’s security.
- Remote Code Execution: This leads to RCE, allowing us to execute system commands on the server.
Final Thoughts on the PicoCTF 3v@l Walkthrough
Congratulations! If you followed this PicoCTF 3v@l walkthrough, you’ve successfully exploited a vulnerable eval() function to get Remote Code Execution and grab the flag. But remember, this is just the tip of the iceberg. There are countless other web challenges out there that require similar techniques to bypass filters, execute commands, and break into vulnerable systems.
If you enjoyed this challenge and want to level up your hacking skills, check out more picoCTF challenges. But always remember, ethical hacking is the way to go—test your skills in controlled environments, and never misuse your newfound power.