wellcome to picoctf challabge, i currently i write writeups for picoCTF challenges , in this challage , its about hash cracking
Overview of this picoCTF hash crack
Challange: hashcrack
Author: Nana Ama Atombo-Sackey
Description: A company stored a secret message on a server which got breached due to the admin using weakly hashed passwords. Can you gain access to the secret stored within the server?Access the server using nc verbal-sleep.picoctf.net 61522
Hints:
- Understanding hashes is very crucial. Read more here.
- Can you identify the hash algorithm? Look carefully at the length and structure of each hash identified.
- Tried using any hash cracking tools?
Access the server Using Netcat
netcat is network communnication tool, its commonly used for interacting with remote servers.
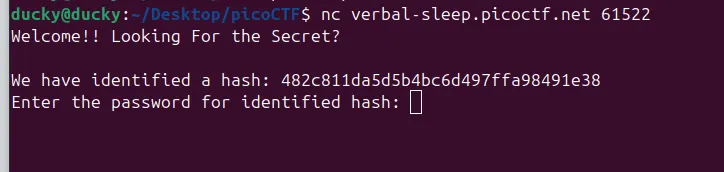
nc verbal-sleep.picoctf.net 61522
when run this command , i got remote interaction interface like this
Welcome!! Looking For the Secret?
We have identified a hash: 482c811da5d5b4bc6d497ffa98491e38
Enter the password for identified hash:
move to next step.
Analysing Hashing type
We need to identify the hashing type. Several methods are available for this, such as online hash identifier tools and local tools like HashID, Haiti, and others. Many different tools are available for this task.
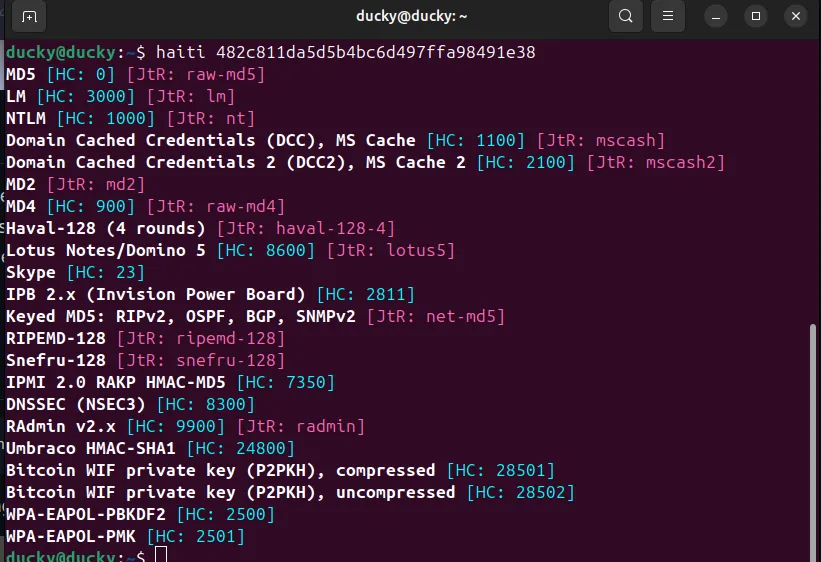
i use this haiti tool for identify hash type, its gives most probable hash types
Cracking the hash
In the previous tasks, we identified the hash type. Now, let’s crack the hash. I will use Hashcat to crack this hash.
hashcat -m 0 -a 0 <hash_file> <wordlist_file>
in this command -m is a method and 0 is defined md5 hashing, in this command -a is defined attacker mode , 0 is indicate dictionary attack , and the add your hash_file and directory wordlist file.
But in this challenge, I will use CrackStation, an online web application. It uses the most common hashed wordlist, and the website automatically identifies the hash type and reveals the real value.
Cracking hash 1
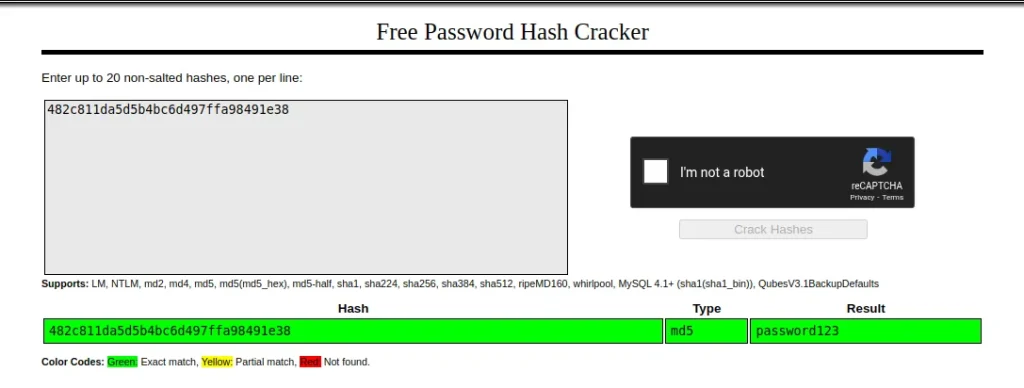
hash passwordis password123,
after cracking this hash, when i enter in this terminal , its again show another hash,
We have identified a hash: 482c811da5d5b4bc6d497ffa98491e38
Enter the password for identified hash: password123
Correct! You've cracked the MD5 hash with no secret found!
Flag is yet to be revealed!! Crack this hash: b7a875fc1ea228b9061041b7cec4bd3c52ab3ce3
Enter the password for the identified hash:
Cracking hash 2
again i use crackstation for cracking this hash,
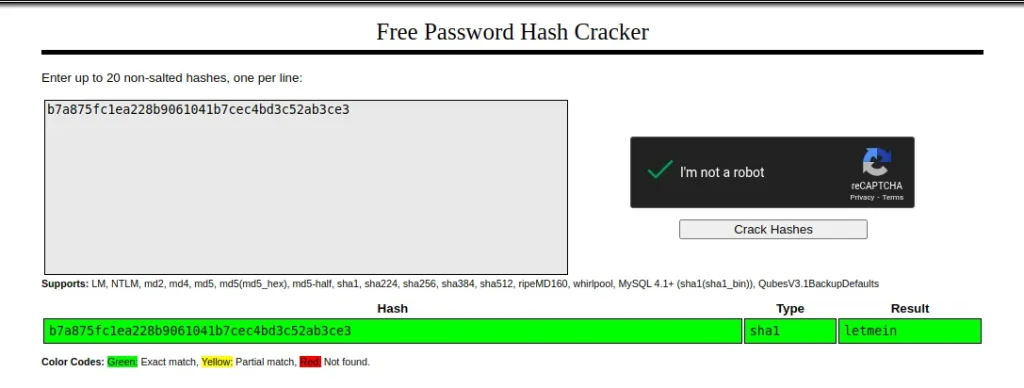
| b7a875fc1ea228b9061041b7cec4bd3c52ab3ce3 | sha1 | letmein |
when i this its again give another hash value so
Enter the password for the identified hash: letmein
Correct! You've cracked the SHA-1 hash with no secret found!
Almost there!! Crack this hash: 916e8c4f79b25028c9e467f1eb8eee6d6bbdff965f9928310ad30a8d88697745
Enter the password for the identified hash:
Cracking hash 3
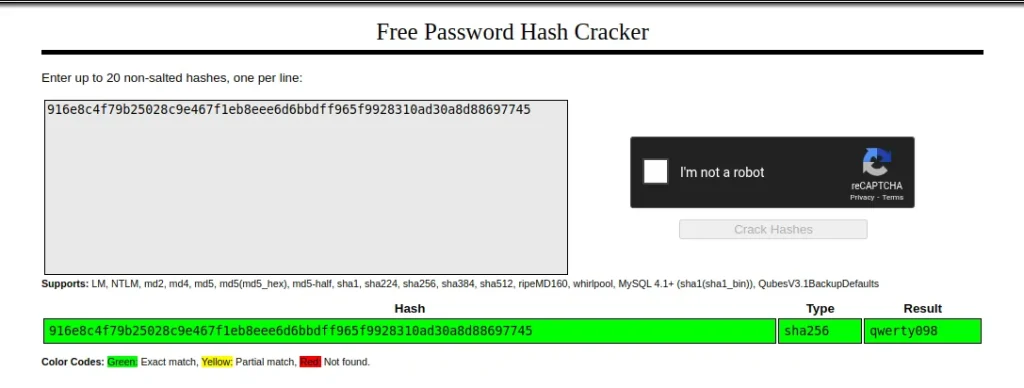
this was final hash i got a flag
Enter the password for the identified hash: qwerty098
Correct! You've cracked the SHA-256 hash with a secret found.
The flag is: picoCTF{UseStr0nG_h@shEs_&PaSswDs!_36a1cf73}
thank you for reading this blog