Welcome to the picoCTF heapdump challenge! In this challenge, you’ll explore a web application and find an endpoint that exposes a file containing a hidden flag. This post will guide you through the steps to uncover the flag by exploring the backend and using basic tools to analyze the server’s memory.
picoCTF heapdump challenge overview
challange : head-dump
Author: Prince Niyonshuti N.
Description : Welcome to the challenge! In this challenge, you will explore a web application and find an endpoint that exposes a file containing a hidden flag.The application is a simple blog website where you can read articles about various topics, including an article about API Documentation. Your goal is to explore the application and find the endpoint that generates files holding the server’s memory, where a secret flag is hidden.The website is running picoCTF News.
hints :
- Explore backend development with us
- The head was dumped.
In this challenge, we need to explore the web application and all its endpoints, including all the links. The challenge already provides hints to guide us.”
Exploring the Web application
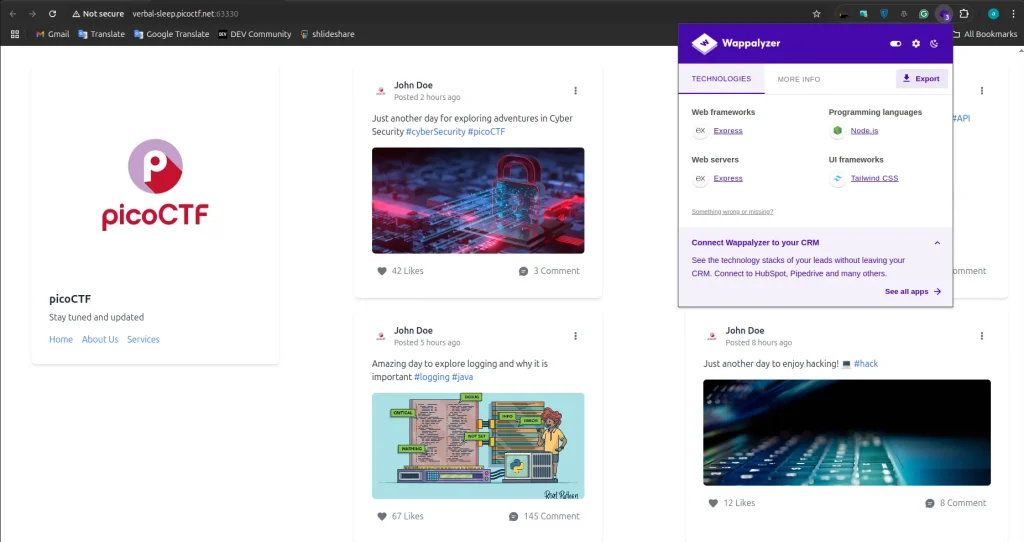
In this challenge, it’s a simple blogging website. I used the Wappalyzer Chrome extension to analyze the technologies used to build the web application.
The results from Wappalyzer show that this web application uses the Express web framework and Express server, with Node.js for programming. It also uses Tailwind as the UI framework.
On this website, I clicked all the links. When I clicked on API Documentation, it redirected me to ‘/api-docs,‘ which is hosted on Swagger UI.
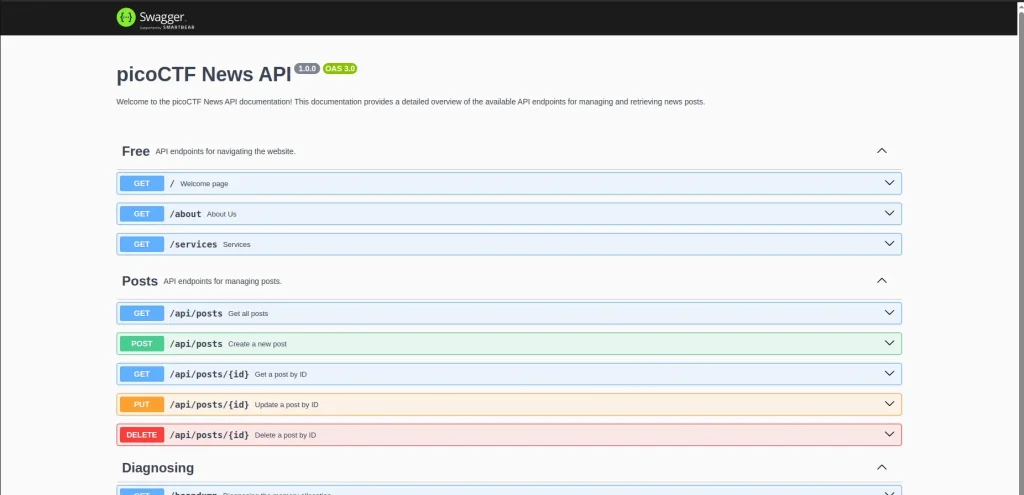
Finding the Endpoint and Execute
in this Swagger docs shows some routes , i can be execute some routes, but i dont need to execute all the routes beacuse they give hints.
- The head was dumped.
just i i try this /heapdump to execute it
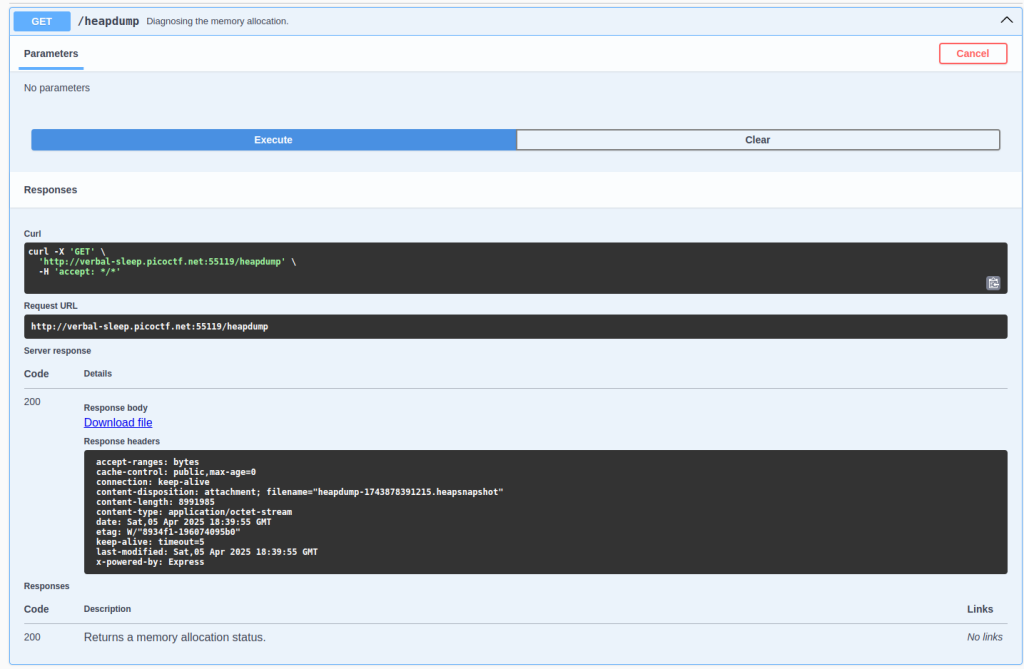
Using Swagger’s “Try it out” feature, I triggered the /heapdump endpoint. This action downloaded <> .heapsnapshot file containing the server’s memory data.
Finding Flag from downloaded file
after download this, its a huge text file, we need to extract flag from this text.
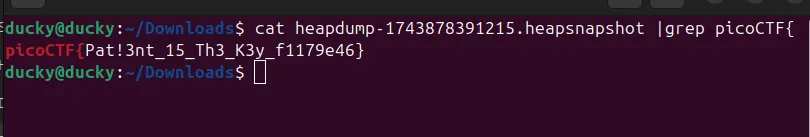
so we can use this bash command for filter this flag
cat heapdump-1743878391215.heapsnapshot |grep picoCTF{
Conclution
In this PicoCTF challenge, we explored a simple web application and discovered the /heapdump endpoint using the Swagger UI. This endpoint allowed us to download a .heapsnapshot file containing the server’s memory data.
Although the file was massive, we used a simple bash command to filter out the flag. Running the command cat heapdump-1743878391215.heapsnapshot | grep picoCTF{ helped us quickly find the hidden flag.
This challenge was a great way to practice exploring web applications, understanding backend endpoints, and using basic tools to extract hidden information. It’s a valuable lesson in web application security and how to handle large data files effectively.