If you’re here, it means you’re probably stuck on the PicoCTF Local Authority challenge. Well, don’t worry – we’ve got you covered! Let’s break this down with some fun and a sprinkle of humor, so you can get that sweet flag.
What is PicoCTF?
First things first – PicoCTF is a Capture The Flag (CTF) competition that tests your hacking skills in a fun, educational way. Each challenge comes with a twist, and your job is to exploit vulnerabilities and solve puzzles to capture the “flag.”
But the Local Authority challenge? Oh, this one’s a bit cheeky. Let’s get into it.
The Setup: What You’ll See
1. The Login Page
When you first visit the website for the Local Authority challenge, you’ll be greeted with a basic login form. You know the drill: username, password, the usual suspects. But nothing looks too suspicious… right?
2. The Burp Suite Reveal
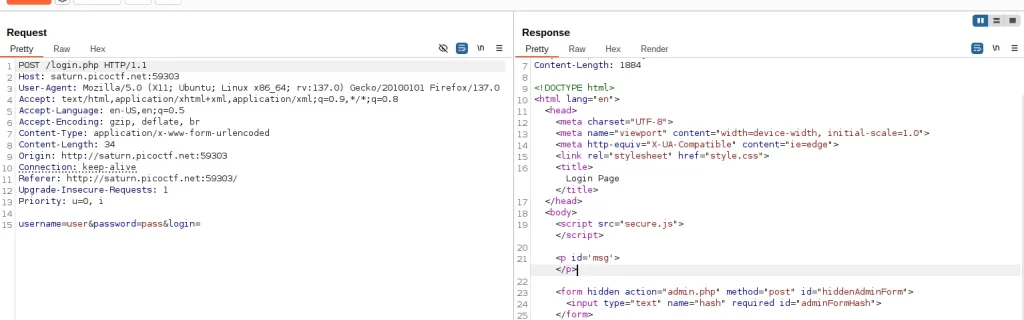
Ah, the magic of Burp Suite! This tool is your best friend when it comes to web security challenges. So, after you log in with random credentials (you didn’t expect to actually get in, did you?), Burp Suite grabs the traffic and lets you have a peek under the hood.
The Discovery: A Tiny Gem in the Code
1. The Secure.js File
While digging through the captured traffic, you find a file named secure.js. Now, most people would panic, but you? You’re a seasoned CTF player. You know that this file is where the magic happens. Inside, you discover this little beauty:
function checkPassword(username, password)
{
if( username === 'admin' && password === 'strongPassword098765' )
{
return true;
}
else
{
return false;
}
}

2. The Big Reveal (PicoCTF Local Authority )
Boom! There it is. The username admin and password strongPassword098765 are sitting there in plain sight, like someone left the front door wide open.
You might have felt like Sherlock Holmes for a second. Don’t worry – we all do!
Solving the Challenge: Enter the Credentials
Now that you’ve got the username and password, it’s time to put them to work. Head back to the login page, enter admin as the username and strongPassword098765 as the password.
When you hit Login, you’ll be rewarded with the flag. It’s that easy. The flag is:
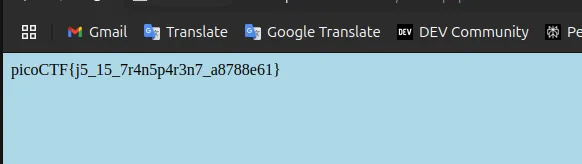
picoCTF{j5_15_7r4n5p4r3n7_a8788e61}
Key Takeaways from the Local Authority Challenge
- Simple code, big discovery: Sometimes, the solution is right in front of you, hidden in plain sight.
- Burp Suite is your best friend: Capturing and analyzing traffic is a vital skill in web security challenges.
- Password management is crucial: If you learn nothing else, remember to keep those passwords under wraps.
Why This Challenge is Awesome (and Funny)
This challenge is a great example of how CTFs can sometimes be simple yet hilarious. You spend all that time thinking there’s a huge trick, only to realize that the password is right there in the code. It’s like finding out the answer to a math problem was written on the back of your math notebook the whole time. Classic!
But that’s what makes it fun, right? There’s no feeling quite like the moment when everything clicks.
Wrapping Up
And there you have it! The PicoCTF Local Authority challenge solved with a little detective work, a dash of humor, and a lot of caffeine.
You’ve learned:
- How to capture and analyze traffic with tools like Burp Suite.
- How to spot hidden passwords.
- And, most importantly, you got that sweet flag!
Now go ahead and share this walkthrough with your fellow CTF enthusiasts. Who knows, maybe they’ll need a laugh after they find out how simple this one was!
Additional Resources
For more on web security, password management, and Burp Suite tutorials, check out these top resources:
That’s it for the PicoCTF Local Authority walkthrough! Until next time, happy hacking!