Welcome to the PicoCTF Scavenger Hunt Walkthrough, where we take you step-by-step through the process of uncovering each part of the flag. Trust me, it’s a hilarious ride as you follow the trail of clues and hidden files. This scavenger hunt may seem like a fun challenge, but it hides some tricky puzzles, and I’m here to make sure you don’t get lost! 🎉
Viewing the Source Code (PicoCTF Scavenger Hunt Walkthrough)
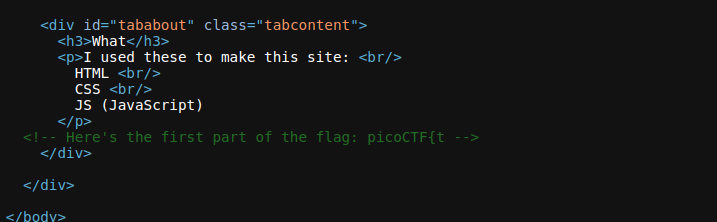
Alright, let’s start our quest. The first thing you’ll need to do is view the source code of the website. To do that, just right-click and hit “View Page Source”. In the source code, I immediately stumbled upon the first part of the flag, and boy, was it a huge hint.
Here’s a snippet from the source code:
HTML <br/>
CSS <br/>
JS (JavaScript)
</p>
<!-- Here's the first part of the flag: picoCTF{t -->
</div>
Next Step: Uncovering Hidden Clues in the CSS File
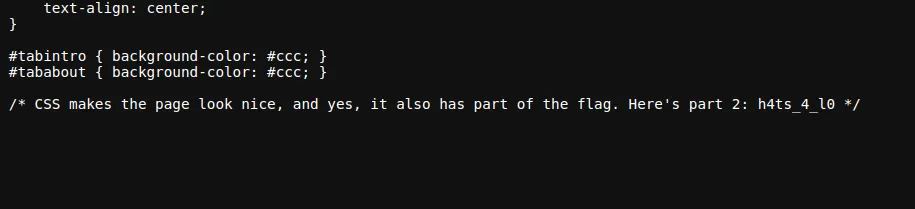
Now that we’ve cracked the first part of the flag, let’s move on to the CSS file. The website uses a simple stylesheet, but guess what? It contains the second part of the flag!
Here’s the line that gave it all away:
/* CSS makes the page look nice, and yes, it also has part of the flag. Here's part 2: h4ts_4_l0 */Second flag part: h4ts_4_l0
Finding Clues in the JavaScript File
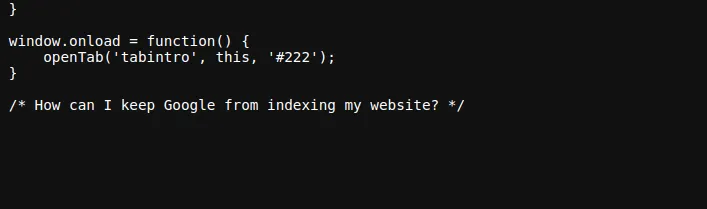
Now, let’s dive into the JavaScript file. I was expecting to find more juicy details here, but instead, all I found was a big clue. The comment in the JavaScript file made me question my entire existence (well, not really, but it made me think for a second)!
/* How can I keep Google from indexing my website? */That comment led me to robots.txt, the hidden treasure trove of clues. But before I get ahead of myself, let’s move on to the next step.
The Robots.txt File: The Gateway to More Clues
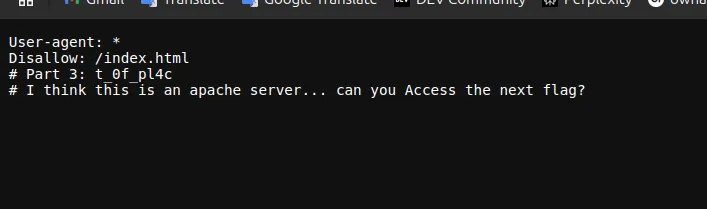
I visited the robots.txt file, and BOOM, there it was: the third part of the flag. Here’s the content I found:
User-agent: *
Disallow: /index.html
# Part 3: t_0f_pl4c
# I think this is an apache server... can you Access the next flag?Third flag part: t_0f_pl4c
Digging Deeper with .htaccess Files
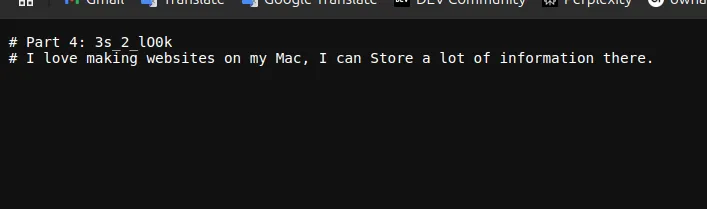
What’s better than a .txt file full of clues? A hidden .htaccess file! This is where things start to get seriously fun. In the .htaccess file, I found the fourth part of the flag:
# Part 4: 3s_2_lO0k
# I love making websites on my Mac, I can Store a lot of information there.
Fourth flag part: 3s_2_lO0k
The Mac Secret: Finding the Fifth Flag
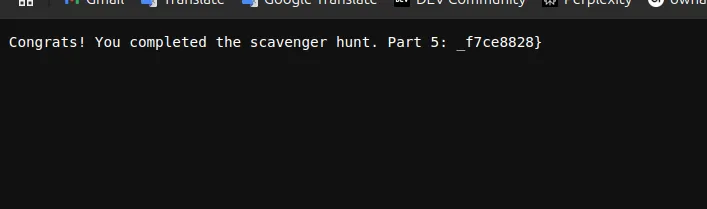
If you’re a Mac user, you know about .DS_Store files. These pesky little files store meta-data about the folders they reside in. But guess what? They’re not just annoying—they’re part of the treasure hunt!
After some digging, I found the final clue in the .DS_Store file. And with it, the fifth and final flag:
Congrats! You completed the scavenger hunt. Part 5: _f7ce8828}Fifth flag part: _f7ce8828}
The Full Flag (PicoCTF Scavenger Hunt Walkthrough)
After all that effort, I had all five parts of the flag! Here it is, the complete flag:
picoCTF{th4ts_4_l0t_0f_pl4c3s_2_lO0k_f7ce8828}And just like that, you’ve completed the PicoCTF Scavenger Hunt. You didn’t need to brute-force your way through this one, did you? You just needed some good ol’ detective work, and maybe a few good laughs along the way.
Conclusion: A Hilarious Yet Challenging Adventure
In the end, this PicoCTF Scavenger Hunt was a blend of fun, frustration, and discovery. From diving into source code to uncovering hidden files, you learned some valuable tricks that can help in future challenges.
So, what’s the takeaway here? A great scavenger hunt isn’t just about finding flags—it’s about enjoying the process, laughing at the challenges, and learning a thing or two along the way.